Zero Trust Architecture: The Strategic Imperative for Future-Ready Enterprises
January 24, 2026
Clear insight into competitor positioning and market share.

As enterprises continue to expand their digital ecosystems and face increasingly sophisticated threats, Zero Trust Architecture (ZTA) is emerging as a foundational strategy for resilient and adaptive cybersecurity. ZTA will mature with hyper-automation, facilitating self-enforcing policies, real-time threat detection, and adaptive network segmentation. Quantum-proof cryptography will protect identity verification and key exchanges across all sessions, extending trust to machine-to-machine (M2M) and IoT ecosystems. With the help of federated trust models, ZTA will facilitate cross-domain authentication across supply chains and smart cities. This will ultimately create a seamless, self-optimizing security mesh that protects all digital services, transactions and devices in future-proof enterprise ecosystems.
Evolution of Network Security from Perimeter Defense to Zero Trust
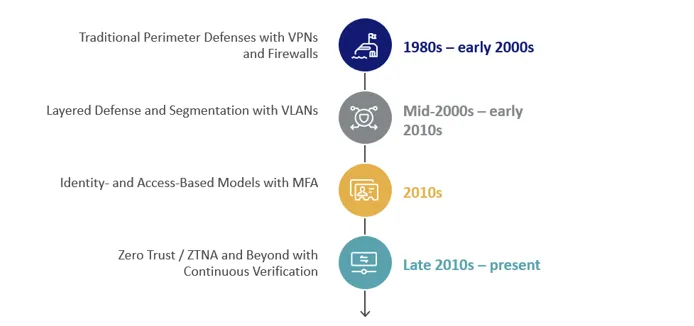
The evolution of cybersecurity architecture illustrates the shift from static, perimeter-based defenses to dynamic, identity- and context-driven models such as Zero Trust Architecture (ZTA and Zero Trust Network Access (ZTNA), which eliminate implicit trust by securing every access transaction.
Traditional Perimeter Defenses (1980s–early 2000s)
In the era of centralized IT and on-premises architecture, the "castle-and-moat" approach was characterized by the use of VPNs, firewalls and Demilitarized Zone (DMZs). The perimeter was well secured, but the users and devices from inside were assumed to be trusted. The assumption that the network was secure from the inside was proven flawed by insider threats and lateral movement attacks.
In the era of centralized IT and on-premises architecture, the "castle-and-moat" approach was characterized by the use of VPNs, firewalls and Demilitarized Zone (DMZs). The perimeter was well secured, but the users and devices from inside were assumed to be trusted. The assumption that the network was secure from the inside was proven flawed by insider threats and lateral movement attacks.
As higher-level threats became more sophisticated, enterprises utilized defense-in-depth with virtual local area network (VLANs), internal firewalls and segmentation domains. This prevented the propagation of attacks within networks but continued to function under partial implicit trust, as internal hosts still periodically interacted without persistent authentication.
With the innovations of work-from-anywhere, Bring Your Own Device (BYOD) and cloud security, the emphasis is on user identity as the new perimeter. Multi-factor authentication (MFA), Role-Based Access Control, and Single Sign-On became the norm. Those static identity models still left open the possibility for trust gaps by inferring that, although users had been authenticated, they would continue to be trustworthy throughout the session.
Modern security architecture rules out implicit trust altogether. Zero Trust continuously checks all users, all devices and all sessions using a dynamic, context-based policy. Where securing the perimeter was the approach, securing every transaction is the new motto. Examples include Google's BeyondCorp initiative and the U.S. federal guidelines (e.g., OMB M-22-09), which assume all access attempts are malicious until proven otherwise.
Figure 6
Evolution of Network Security: From Perimeter to Zero Trust
Source: BCC Research
Zero Trust security has become a foundational approach for modern enterprise cybersecurity strategies. Within this paradigm, Zero Trust Architecture serves as the overarching framework that enforces verification and least-privilege principles across the enterprise, whereas Zero Trust Network Access (ZTNA) focuses on securing application-level connectivity, especially for remote and third-party users. The table below highlights the key differences between ZTA and ZTNA in terms of scope, approach and implementation focus.
Table 1
Key Differences: ZTA vs. ZTNA
|
Aspect |
Zero Trust Architecture |
Zero Trust Network Access
(ZTNA) |
|
Scope |
Comprehensive
security framework for the entire organization. |
Specific
solutions for secure remote access. |
|
Focus |
Policies,
principles and technologies across all assets. |
Granting
access to applications without exposing the network. |
|
Implementation |
Involves
identity, device, network, application and data layers. |
Operates
primarily at the network and application access layers. |
|
Access
Control |
Continuous
verification of all users and devices. |
Provides
granular access to specific applications. |
|
Uses
Cases |
Enhancing
overall security posture. |
Facilitating
secure remote work and third-party access. |
Key Trends in ZTA Adoption
On their ZTA trajectories, some patterns have been the most notable during 2024–2025. The following are three key ones:
- Secure Access Service Edge (SASE) and ZTNA are replacing legacy VPNs by providing identity-based, application-level access that ensures users connect only to approved apps such as CRM. Delivered via cloud-native models, they authenticate users and devices before granting access, preventing unauthorized lateral movement while enabling secure use of necessary tools.
- Micro-segmentation, aided by AI/ML, automatically detects abnormal cross-segment activity and isolates it into secure segments. This enforces strict, identity-based policies at the service level, enhancing network security by limiting unauthorized access within each segment.
- Continuous verification and adaptive trust dynamically assess risk based on device health, location and behavior, automatically blocking suspicious activity such as large data downloads. Endorsed by the U.S. National Security Agency (NSA), this model enables real-time defense and precise control, adapting to evolving threat environments.
Context-Driven Access as the Foundation of ZTA Enforcement
Access must be temporary and context-based as remote and hybrid workforces expand. For example, a consultant working from a coffee shop should not have the same access as when operating from the office; ZTA checks their device and role each time.
Cloud and multi-cloud proliferation is driven by the need to decouple trust from fixed network boundaries. For instance, when a company moves its database from an on-premises server to Amazon Web Services (AWS) or Azure, ZTA ensures access control follows the user, not the data center's perimeter.
ZTA principles are also transforming partner and supply chain integration. The concept is moving from blanket VPN access to fine-grained and trust-based access. For example, the third-party logistics provider has access only to the warehouse management application they need, during work hours, rather than full network access via VPN.
The key idea is that ZTA emphasizes that trust should be continuously verified, not presumed based on initial credentials. This approach prevents attackers from moving laterally within a network even if credentials are stolen, by re-validating each access attempt based on device health, behavior and context.
Existing Solutions and Developments Addressing ZTA Challenges
The section outlines how technology, policy frameworks, vendor alignment and pilot implementations collectively advance Zero Trust adoption and overcome traditional security challenges.
Machine learning enhances ZTA by learning organizational behavior, detecting anomalies in real time, and adjusting access controls dynamically. Research highlights features such as ongoing trust scoring and anomaly detection. Commercial tools, such as Trend Micro, combine micro-segmentation with continuous risk assessment to automate context-aware trust decisions, reducing human error and enhancing security.
The CISA Zero Trust Maturity Model (ZTMM v2.0) provides structured guidance for organizations to adopt and advance zero trust practices across all key domains: identity, device, network, data, application, automation and orchestration. By emphasizing automation and orchestration, it ensures consistent policy enforcement, reduces manual effort, and supports scalable, adaptive security. The ZTMM v2.0 guides organizations from initial implementation to a fully integrated zero trust posture, enabling informed investment decisions and accurate measurement of maturity.
Security vendors are increasingly adopting unified Zero Trust stacks encompassing identity management, access control, micro-segmentation, threat detection and analytics. By conforming to standards such as NIST SP 1800-35, they ensure interoperability, best practices and compliance. This integration simplifies deployment, reduces complexity and delivers a consistent Zero Trust experience across users, devices and applications.
Existing Zero Trust Architecture (ZTA) implementations often start as small pilots, such as those of U.S. federal civilian agencies, to test real-world use cases. CISA's 2025 report highlights the effectiveness, gaps and recommendations from these pilots, providing the industry with a roadmap for widespread adoption with reduced risk.
These advances are diminishing technical uncertainty, providing proven templates, and infusing intelligence into enforcement, bringing ZTA closer to enterprises.
Conclusion
The perimeter-based security model is no longer effective as workloads span clouds, locations and devices. Zero Trust Architecture replaces this with the "never trust, always verify" principle, continuously authenticating users, devices and services based on real-time risk. By enforcing least-privilege access, ZTA reduces attack surfaces, prevents lateral movement and offers integrated visibility, becoming the foundational fabric for secure, resilient digital operations in complex environments.
Looking for Consulting & Advisory Projects
BCC Research Beacon 
